Hello, and welcome to another episode of Continuous Improvement, where we explore the latest trends and technologies shaping our digital world. I'm your host, Victor Leung, and today we're diving into LangChain—a revolutionary framework for building applications powered by Large Language Models, or LLMs.
LangChain has been making waves in the developer community, boasting over 80,000 stars on GitHub. Its comprehensive suite of open-source libraries and tools simplifies the development and deployment of LLM-powered applications. But what makes LangChain so special? Let's break it down.
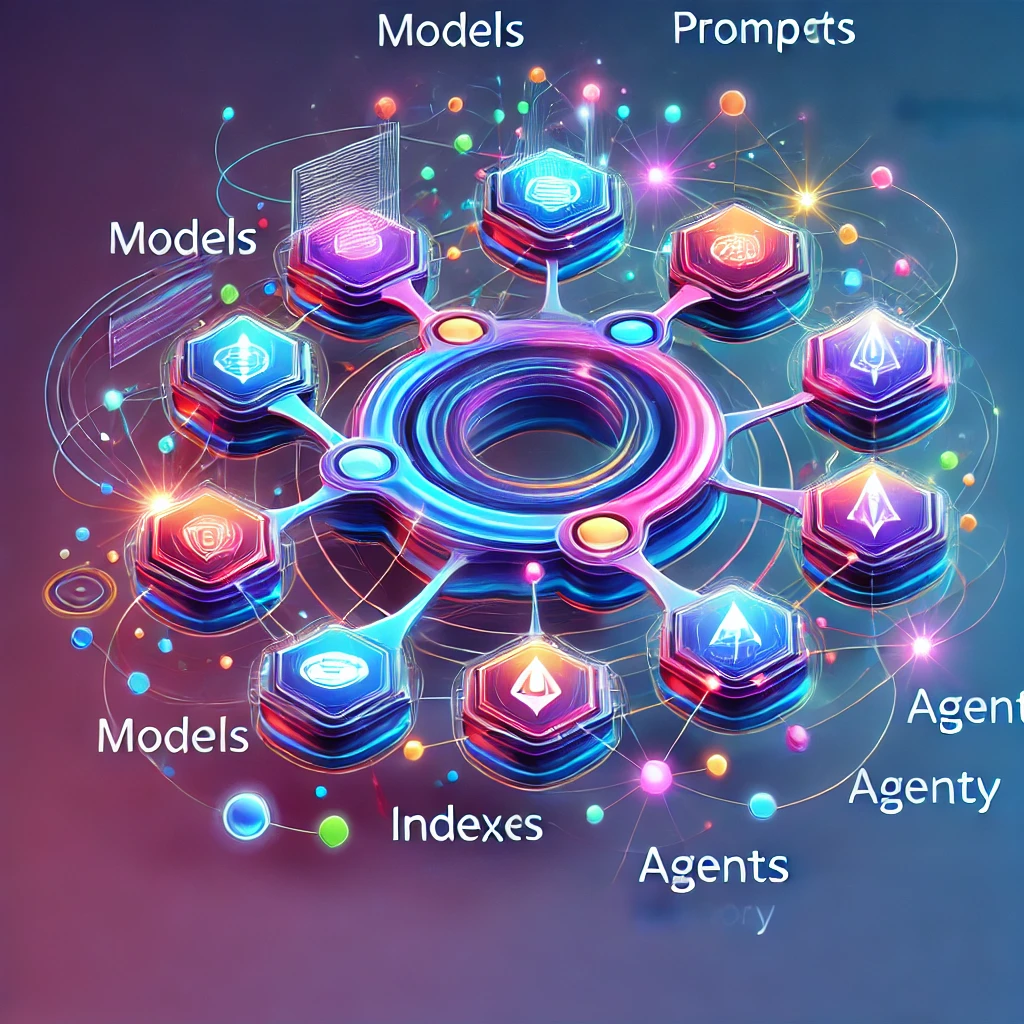
LangChain's strength lies in its modular design, each module offering unique capabilities to streamline your development process.
First, we have the Models module. This provides a standard interface for interacting with various LLMs. Whether you're working with OpenAI, Hugging Face, Cohere, or GPT4All, LangChain supports these integrations, offering flexibility in choosing the right model for your project.
Next up is the Prompts module. This is crucial for crafting prompts that guide the LLMs to produce the desired output. LangChain makes it easy to create, manage, and optimize these prompts, a fundamental step in programming LLMs effectively.
The Indexes module is another game-changer. It allows you to integrate language models with your datasets, enabling the models to reference or generate information based on specific data. This is especially useful for applications requiring contextual or data-driven responses.
LangChain also introduces the Chains module, which lets you create sequences of calls that combine multiple models or prompts. This is essential for building complex workflows, such as multi-step decision-making processes.
Perhaps the most powerful feature of LangChain is the Agents module. Agents are components that process user input, make decisions, and choose appropriate tools to accomplish tasks. They work iteratively, making them ideal for solving complex problems.
Finally, the Memory module enables state persistence between chain or agent calls. This means you can build applications that remember past interactions, providing a more personalized and context-aware user experience.
One of the standout features of LangChain is dynamic prompts. These allow for the creation of adaptive and context-aware prompts, enhancing the interactivity and intelligence of your applications.
Agents and tools are integral to LangChain's functionality. An agent in LangChain interacts with its environment using an LLM and a specific prompt, aiming to achieve a goal through various actions. Tools, on the other hand, are abstractions around functions that simplify interactions for language models. LangChain comes with predefined tools, such as Google search and Wikipedia search, but you can also build custom tools to extend its capabilities.
Memory management in LangChain is crucial for applications that require remembering past interactions, such as chatbots. The framework also supports Retrieval-Augmented Generation, or RAG, which enhances the model's responses by incorporating relevant documents into the input context. This combination of memory and RAG allows for more informed and accurate responses, making LangChain a powerful tool for developers.
LangChain offers a comprehensive framework for developing LLM-powered applications, with a modular design that caters to both simple and complex workflows. Its advanced features, such as dynamic prompts, agents, tools, memory management, and RAG, provide a robust foundation for your projects.
So, if you're looking to unlock the full potential of LLMs in your applications, LangChain is definitely worth exploring.
Thank you for tuning in to Continuous Improvement. If you enjoyed today's episode, don't forget to subscribe and leave a review. Until next time, keep innovating and pushing the boundaries of what's possible.
That's it for this episode. Stay curious and keep learning!